Kerberos
We would like to show you a description here but the site wont allow us. The Kerberos protocol uses strong cryptography so that a client can prove its identity to a server and vice versa across an insecure network connection.

Kerberos Art From Soul Sacrifice Art Artwork Gaming Videogames Gamer Gameart Conceptart Illustrat Fantasy Creatures Mythical Creatures Creature Concept
Share your apps widgets components themes and anything else you have constructed in Mendix.

Kerberos. AGE 21 They dont serve beer in prison so drink responsibly. Launch the next step in your career. IBM X-Force Exchange is a threat intelligence sharing platform enabling research on security threats aggregation of intelligence and collaboration with peers.
Restated kerberos logging should be disabled when not actively troubleshooting. We would like to show you a description here but the site wont allow us. Gain skills advance your career begin your bachelors degree.
A cheatsheet with commands that can be used to perform kerberos attacks - kerberos_attacks_cheatsheetmd. For over 25 years TCO Certified has addressed the worlds most pressing sustainability challenges with many successes. Harper is a top Illinois college and career training school.
Then use the -n option with a principal of the form REALM an empty principal name followed by the at-sign and a realm name. A little toolbox to play with Microsoft Kerberos in C - GitHub - gentilkiwikekeo. Kerberos event logging is intended only for troubleshooting purpose when you expect additional information for the Kerberos client-side at a defined action timeframe.
Created May 14 2019. Kerberos was created by MIT as a solution to these network security problems. When you add data to your password keeper on one device the app automatically sends this data to the cloud and then from the cloud straight to your other devices that have Kaspersky Password Manager installed on them and that are connected to your My Kaspersky account.
For fully anonymous Kerberos configure pkinit on the KDC and configure pkinit_anchors in the clients krb5conf. Bring the best jobs to your students. A little toolbox to play with Microsoft Kerberos in C.
All gists Back to GitHub Sign in Sign up Sign in Sign up message Instantly share code notes and snippets. The Kerberos protocol is an open protocol that is supported by many platforms and vendors. Compare our affordable tuition.
When this protection if enabled it unifies the logic for Resource-Based Constrained Delegation RBCD with the original constrained delegation. Kerberos can also reduce the load on domain controllers. If permitted by the KDC an anonymous ticket will be returned.
Cette page nécessite JavaScript activé pour fonctionner. All outstanding S4USelf Kerberos service tickets must have expired by waiting a day after completing the Windows update deployment to all Active Directory domain controllers. Lets continue the work together.
Kerberos can reduce page latency in certain scenarios or increase the number of pages that a front-end web server can serve in certain scenarios. We would like to show you a description here but the site wont allow us. 4607 Wedgewood Blvd Frederick Maryland.
2018 Flying Dog Brewery. Hire the next generation of talent.

Kerberos Gp1 Jpg Image Cops Group Pictures Jin Roh
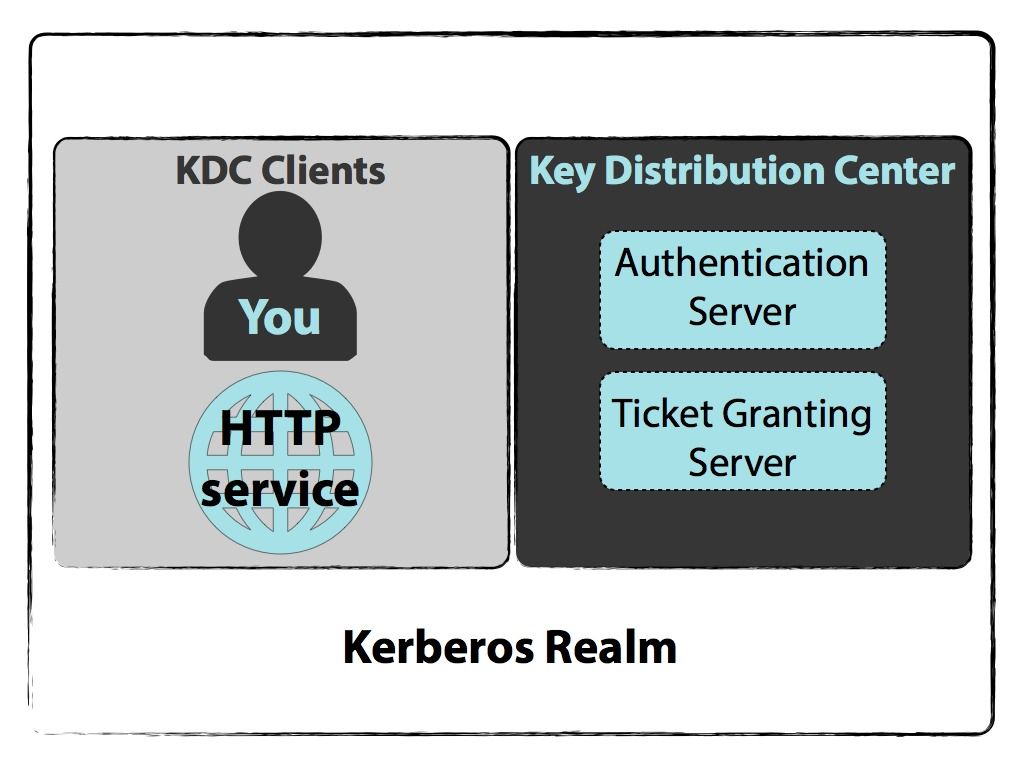
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Kerberos Architecture Computer Help Windows Server Microsoft

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Selecthiveql Nifi Connection Hives

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

Kerberos 예약 완료된 도안입니다 최소크기는 세로 14cm 입니다 Sold Out Minimum Size Is 14cm Vertical Dark Tattoo Greece Tattoo Japanese Tattoo Art

Apache Storm Due To Its Comprehensive Feature Helps Enterprises To Process Data Faster Solving Complex Data Problems In Storm Online Learning Machine Learning

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Kerberos Saga Jager Enemy Character Design

Freeletics Workout Kerberos Das Workout Geht Uber 3 Runden Mit Jeweils 3 Ubungen Pro Runde Freeletics Freeletics Ubungen Freeletics Workout

Kerberos Architecture Computer Help Windows Server Microsoft

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base


Posting Komentar untuk "Kerberos"